With more and more businesses adopting cloud infrastructure to safeguard their critical data, there is also a continued increase in concerns over data privacy and security.

Despite trends such as cloud computing, mobility and virtualization which are enabling various ventures to enhance their agility and flexibility at a fast pace, APTs (Advanced Persistent Threats) like Hydraq and Stuxnet are also bringing forth widespread challenges in the protection of information.
With the numerous security threats looming at such a significant rate, it is now essential for businesses to predetermine data breaches and prevent the attacks from penetrating their systems.
Currently, businesses should implement elaborate cloud security measures to establish a strong data encryption and protection posture.
They need to be versatile and use technologies in their setting like file integrity monitoring, intrusion detection, two-factor authentication and much more.
Also, cloud security is an evolving challenge which can be addressed only if the technologies and tools are structured to grow along with it.
In such scenarios, numerous organizations are looking for a solution to safeguard their cloud architecture and subsequently relying on various solutions to help them curb breaches.
To help you navigate and identify the right cloud security solution, herein is an overview of what these systems do along with a list of options for you to choose from.
What Are Cloud Security Solutions?
Cloud security solutions safeguard data, networks and access by securing data, workloads and apps that are hosted on Cloud infrastructure.
The same servers, software and apps that used to be located on-premises in the previous decades, are now migrated to cloud services, but they still need the same security protection level as before.
Firms use such tools in enforcing policies, protecting information transmitted through or stored in cloud applications. These provisions offer secure access points, like gateways and sandboxes, for only approved users to only launch and subsequently run cloud applications in a safe environment.
Administrators can set permissions, manage governance and monitor anyone accessing and using the applications. Numerous cloud security solutions offer data loss prevention controls and encryption to safeguard further data and documents stored within cloud applications.
Numerous cloud security solutions operate like secure email gateways and secure web gateways. While they may offer similar access points, they also serve to safeguard entire application networks as opposed to just email documents or server data.
Why Choose Cloud-Based Security Solutions?
Notwithstanding the size of your business, whether a small enterprise or a large corporation, provided you have access to the internet, you remain susceptible to cyberattacks.
As such, there is a need to stay vigilant and safeguard your network from malicious attackers, and among the best ways to guarantee this is to adopt cloud security solutions since they are essential for protecting cloud-hosted data.
These solutions help you secure your data as follows:
- Cloud security features improve the monitoring and tracking of attacks in a global scale compared to non-cloud security solutions. They offer signature and real-time firewall updates, blocking unsafe traffic protection etc.
- Offers 24/7 live tracking and security of websites, APIs, serverless apps, containers etc through continuous monitoring and web application attack protection.
- Aside from network and application scanning, cloud security solutions also enhance application speed performance through resources that can scale-up on demand.
Having identified the benefits of cloud security solutions, here are some of the best cloud security solutions in the market today.
1. Check Point CloudGuard
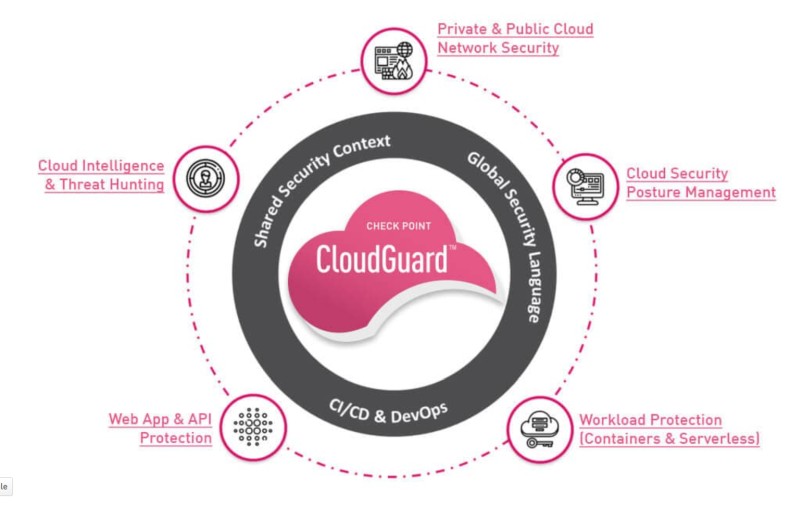
Checkpoint is one of the most trusted vendors and manufacturers of network firewalls and other security products. This Israeli company focuses on creating security solutions for any business market.
CloudGuard, Checkpoint’s product for securing multi-cloud environments, is a context-based cloud security engine supporting many different cloud environments such as AWS, Azure, Vmware, Oracle etc.
Rather than having multiple components of security control products, CloudGuard takes a unified approach to threat prevention and posture management from a unified platform.
The product includes also API protection so malicious actors can’t abuse your services. It also comes with both private and public cloud security and monitoring, and it actively hunts for new threats on the horizon. Notably, CloudGuard supports also security for containerized and serverless apps.
Teams can take advantage of the DevSecOps that’s offered. This allows for seamless and continuous integration of good security practices with software in development, lessening attack surface.
2. CloudPassage Halo
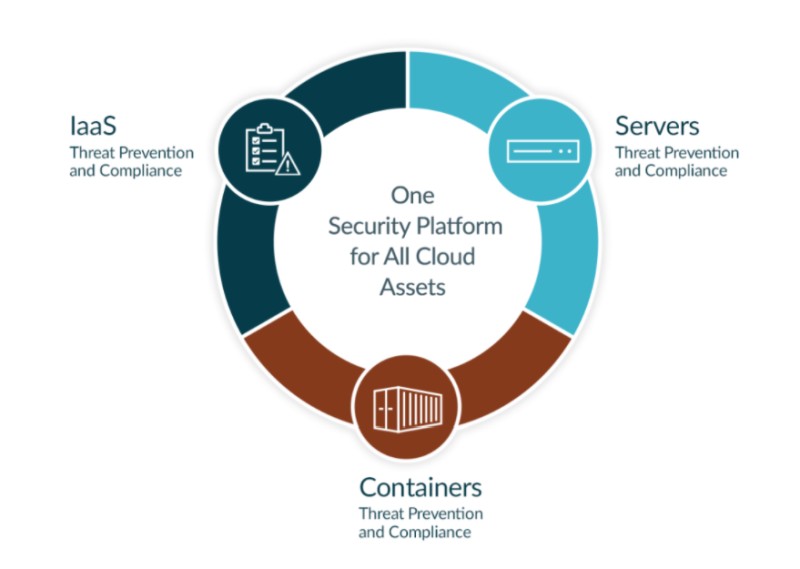
CloudPassage aims to be a unified security platform for all of your cloud assets such as Public IaaS (Infrastructure as a Service), Cloud Servers and Containers.
It works on the principle that proactive security is a better approach than vendor-level endpoint security.
This safety-first philosophy helps prevent zero-day attacks even if the vendor can’t issue a hotfix quickly enough.
The Halo product comes in three different services as below:
- Cloud Secure: Cloud security posture management (AWS, Azure, Google cloud).
- Server Secure: Cloud workload protection platform (Linux and Windows)
- Container Secure: Security for Docker, Kubernetes and CD
It works on the Infrastructure-as-a-Service (IaaS) level (for both private and public cloud infrastructures) and also covers hybrid environments.
Likewise, CloudPassage works at the bare metal level to ensure server-level compliance with industry standards. Beyond that, it supports most containerization, giving users three layers of cloud security.
CloudPassage can be used by employees all the way from junior-level engineers through the C-suite.
For example, Cloud Security Engineers and DevOps Engineers can easily review reports to help them determine faster, more secure workflows and procedures.
Cloud Architects can use the all-in-one solution to easily manage multiple layers of security. Even executives can benefit from data-intensive reports on audit compliance and form a better line of communication with their DevOps teams.
3. Threat Stack Cloud Security Platform
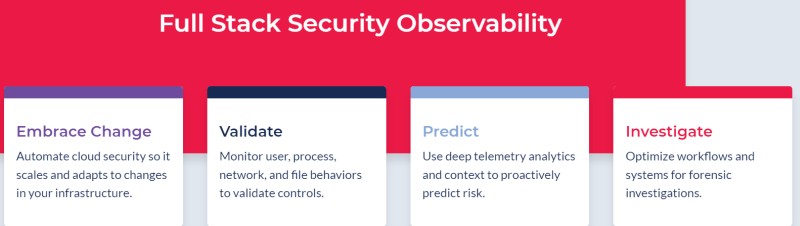
Threat Stack’s platform is designed to both secure your cloud and give your team the most information both observable and concise.
This solution is mostly focused on monitoring your security, what they call as “observability” in DevOps terms.
With a special focus on containerized cloud applications, their security platform operates on five layers of monitoring and observability: the application itself, container orchestration (how your container behaves as it launches), the container itself, the hosting server, and a customized cloud security management console.
By offering observable security suggestions and shortcomings, Threat Stack helps teams identify vulnerabilities before hackers do.
Even if a security incident does arise, the platform can help Cloud Security Engineers figure out what’s going on faster and respond more quickly and accurately.
International regulatory and legal compliance is also tracked, helping ensure that the customer is fully covered.
Finally, Threat Stack prides its platform on the fact that regardless of what the “flavor of the month” is with containerization, it only has one focus: cloud security.
4. Symantec Cloud Workload Protection
Security giant Symantec’s cloud product goes beyond security. Supporting all major cloud computing platforms with “adapters” for their product (AWS, Azure, Google), Cloud Workload Protection (CWP) can automatically scale up and down as workload resources scale up and down as well.
CWP in short is for protecting your workload instances that run on the popular Cloud Providers. To do this, an agent must be installed on each workload instance in order to monitor and enforce the security policies to the instance.
Security-wise, the software has a three-pronged approach. First, it simply “listens” to incoming and outgoing traffic and records anomalies. Second, it analyzes situations using a recommendation engine, providing real-time feedback and even automatic reconfiguration to prevent attacks. Third, it “acts” by automatically deploying whatever is necessary, provided it has the permissions to do so.
A key CWP feature is that everything on the workload is controlled and secured by the agent, such as zero-day threats, file integrity monitoring, host-based IPS, vulnerability protection etc.
With everything “baked in” through native cloud adapters, developers can “set it and forget it” until there’s an incident requiring manual attention.
5. Datadog
Datadog sells and maintains only its flagship product, unlike some of its competitors, which is centered around monitoring (for performance, security etc.)
Marketed as “Cloud Monitoring as a Service” (CMaaS), Datadog’s goal is to combine proven security practices with modernized reporting infrastructure.
Regardless of how servers hosting a cloud-based application are configured, Datadog creates a “deep-dive” view of what’s really happening behind the scenes.
Anyone authorized to can use the platform to see real-time statistics on database queries, server cluster uptime, resource usage, and even suggestions for improvements as development continues.
Individual container instances can be debugged if an application is experiencing problems. All of these operations are performed at the GUI level.
Regarding security monitoring, Datadog helps you identify potential threats to systems in real-time. Your applications and network can send logs to Datadog which parses and enriches these logs in order to extract security information and metrics.
6. Hytrust

HyTrust offers three different product categories for security:
- CloudControl: For workload protection (advanced access control, policy enforcement, forensics etc).
- DataControl: Workload encryption at-rest.
- Key Management: For managing the encryption keys of workload encryption service.
HyTrust workload encryption is designed for applications handling sensitive data in the cloud. Its workload encryption services work with both in-house, physical servers and all major cloud platforms.
Rather than simply encrypt databases and salt them, HyTrust’s platform automatically granularly encrypts each container and virtual machine and contents within them.
With so many layers of data control, it’s almost impossible for hackers to steal this information even if there is a security incident.
Regardless of where an application is hosted, HyTrust provides a full suite of keying tools, including complete key management and even cloud-based rekeying on the fly. It can also be easily ported from one cloud provider to another.
7. PaloAlto Prisma

Given that seven out of the top ten Fortune companies utilizing PaloAlto’s Prisma security platform, there’s a reason the product is so well-known. This is that Prisma truly does it all, from analytics reporting to threat prevention.
Prisma’s Posture Management services allow for both regulatory compliance measures and threat detection.
With a combination of a user and entity behavior analysis engine and/or signature-based antimalware crawler, cloud apps remain secured. Working from a server level, virtual machine level, and container and headless level, no layer is forgotten.
Cloud Network Security that supports full and partial network segregation allows for network engineers to truly define secure data transmission.
Other features, like identity management, layer seven (web application network layer) level security, and API protection as well as a sleek reporting infrastructure make this truly an all-in-one cloud security solution.
8. Fortinet
Fortinet’s cloud security products place an emphasis on application portability on any cloud platform. This gives development teams the most breathing room regarding changing hosting providers, should the need arise.
With Fortinet, Cloud Engineers can have full visibility of the current state of security of their applications. With their Security-as-a-Service API, developers can easily hook existing products into Fortinet’s native cloud adapters. With its unique application layer tools, even Office365 data is protected.
Fortinet offers a unique “Cloud Security Hub” with all the reports and analytics Cloud Architects need.
Using FortiCASB you can have SaaS visibility and control and using FortiCWP you can deploy IaaS visibility and control as well.
9. Cisco Cloud Security

While most of its competitors sell all-in-one solutions, Cisco allows teams to pick and choose individual cloud security components and products if they simply need to complete an already-existing partial security solution.
For example, some cloud security products offered by Cisco include:
- Cisco Umbrella: for secure cloud access
- Cisco Cloudlock: protection of SaaS applications
- Cloud Email Security: blocks and remediates email threats
- Stealthwatch Cloud: monitors IaaS instances
- AppDynamics: application performance monitoring
Teams who develop SaaS apps can utilize Cisco’s SaaS application security. Threats can be easily detected and thwarted, as Cisco provides real-time security alerts. Setting security aside, teams can also take advantage of AppDynamics, which allows developers to easily view performance and resource metrics.
With multi-cloud network protection and workload protection, teams developing apps on public, private, and hybrid clouds can all benefit.
In addition, Cisco provides email security, assistance with securing remote workers’ machines, and many other tertiary security solutions.
10. Lacework
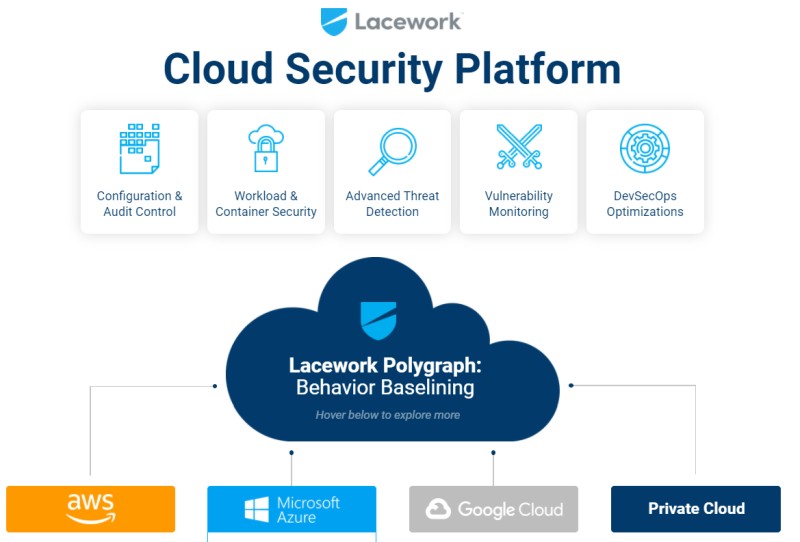
Lacework’s cloud security platform takes a top-down approach to securing all types of cloud-based apps, containerized or not, and on any major platform.
The “Lacework Polygraph” establishes “normal” baseline behavior, which is used to later determine potential behavior anomalies. This allows for potential attacks to be detected even if there’s no signature match.
Lacework’s overall infrastructure monitoring makes it easy for Security Engineers to identify shortcomings and fix them. Artificial intelligence makes alerts more informative than average and doesn’t clog developers’ inboxes.
Finally, Lacework has a suite of applications to assist with security. For example, their “Configuration and Audit Control” application allows developers to set compliance and legal requirements for which the tool will regularly scan.
Workload and container security, advanced threat protection, and vulnerability monitoring all can be viewed granularly, as well. Lacework’s unique “DevSecOps” tool makes adding cybersecurity to the workflow easy.
11. CipherCloud
CipherCloud is a cloud security solution company established in 2010. It operates across three distinct models—PaaS, SaaS and IaaS.
CipherCloud offers a single platform that secures sensitive customer information across multiple private and public cloud applications without compromising on performance or functionality.
Features:
- It provides services across multiple sectors, including telecommunications and government. It safeguards essential cloud applications such as OneDrive, Google Drive, among others.
- It also facilitates data loss prevention, cloud computing as well as related security, cloud encryption gateway, among others uses.
12. Qualys
Qualys is a secure cloud security solution provider which was started in 1999. It provides security to your devices and compliance assets as well as related services. It facilitates data protection through identifying compromised assets and handling them accordingly.

This solution secures your web apps and devices while assisting you to stay compliant through its exclusive cloud-only solutions (needs no software or hardware). The firm assesses threat data to ensure nothing penetrates your system.
Features:
- Qualys provides end-to-end solutions such as cloud infrastructure security, endpoint security, web app security, DevSecOps, compliance, among others—ensuring your teams stay in sync with one another.
- Offers reliability and security across both private and public clouds, threat protection, vulnerability management, monitoring, file integrity, among other utilities.
13. Sophos
A renowned security firm, Sophos was started in 1985 and offers cloud solutions such as firewall, encryption, web and mobile security, antimalware, among others. It offers a cloud-based console known as Sophos Central.
Features:
- Sophos Central offers runtime protection against attacks such as ransomware, mitigating exploits within the web, preventing external DLLs to load, plugins, java applications, among others.
- Provides security solutions designed to suit email, web, mobile, wireless, web servers and other platforms.
14. Proofpoint
Proofpoint. although best known for its email security solution, is another cloud-based security provider which offers protection against numerous cybersecurity threats. Proofpoint’s services are customized for all sizes of businesses.
When considering security vectors (holes within a network that provide a leeway for bad actors to access the system), one of the weakest points is email. Proofpoint precisely works on email security management so customers can ensure their systems are free of threats.
Aside from ensuring nothing risky gets in, Proofpoint also safeguards even outgoing data. Furthermore, it also guarantees that while it preserves to avoid loss of data, it comprises no keys for decrypting any information.
Features:
- Offers email, SaaS, protection against attacks from typical email attachments as well as a mobile solutions from targeted cyber vulnerabilities.
- It safeguards sensitive and essential business data by providing cloud email security solutions to all sizes of businesses and brands.
15. SiteLock
SiteLock was started in 2008 and secures more than 21 million websites across the world. SiteLock is a cloud-based security firm which safeguards sites from attacks, malware and other cyber threats.
Features:
- SiteLock provides website protection by scanning vulnerabilities, identifying and eradicating malware.
- It safeguards against attacks such as SQL, DDoS and XSS.
SiteLock offers dynamic and static caching, load balancing and a global Content Delivery Network (CDN), thereby boosting and enhancing website performance.
Final Word
Different cloud security products boast different pricing and features. When choosing an exclusive security solution, it is essential you identify your particular needs and then select a solution that best covers these needs.
However, and most importantly, ensure that the solution you ultimately settle for offers you adequate monitoring and support.
What’s more, if you are a new startup and are yet to identify the precise cloud security solution you can invest in, you can fundamentally start with selecting an effective cloud hosting program. Adequate cloud hosting can also work well in offering you added security from attackers.
Author
Sophie is a marketing specialist at Security Gladiators. A writer by day and a reader by night, she is specialized in tech and cybersecurity. When she is not behind the screen, Sophie can be found playing with her dog.
Have you reviewed Silent Breach’s cloud services? We’re working with them, and would curious to see how they stack up
John,
Unfortunately I haven’t reviewed Silent Breach. What’s your impression after using their services?
Excellent.
Cloud services are excellent. Enhances speed and saves time .